Cybersecurity Incident Handling Guide
Cybersecurity incidents are inevitable in today’s threat landscape, making effective incident response a critical capability for any organization. Whether you’re building a security operations center, responding to breaches, or preparing for NIST compliance, understanding how to handle incidents systematically can minimize damage, reduce recovery time, and preserve evidence for legal or forensic purposes.
I’ve created a comprehensive repository that walks you through cybersecurity incident handling based on NIST’s “Computer Security Incident Handling Guide” (Special Publication 800-61). This guide serves as your roadmap—directing you to each resource and explaining how to build a robust incident response capability.
What’s Inside
This repository contains six detailed modules covering the complete NIST incident response lifecycle, from foundational concepts to post-incident analysis and continuous improvement. Each file provides practical guidance following NIST SP 800-61 recommendations that you can implement immediately in your organization.
The NIST Framework Approach
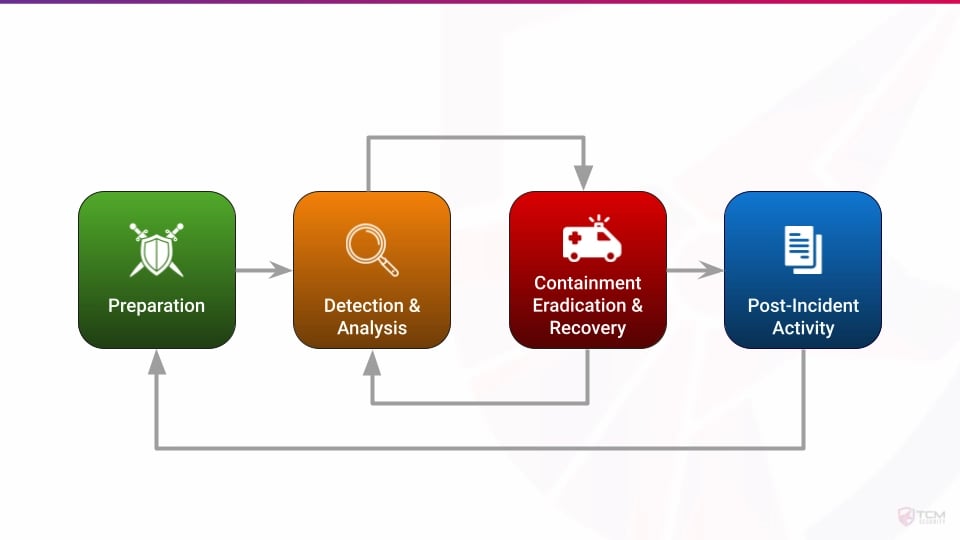
This repository follows NIST Special Publication 800-61, which provides a structured methodology for handling cybersecurity incidents that has been adopted by organizations worldwide. The NIST framework emphasizes that incident response is not merely a reactive process but a continuous cycle of preparation, detection, response, and improvement.
Unlike linear approaches, NIST recognizes that containment, eradication, and recovery often overlap in real-world scenarios. Organizations should not wait to contain all threats before beginning eradication—if additional threats are discovered, they should be contained and eliminated immediately.
Building Your Incident Response Capability
Effective incident response requires more than just technical skills. Throughout these modules, you’ll learn to create comprehensive incident response policies that define what constitutes a security incident and establish organizational authority, develop detailed procedures that your team can follow during high-pressure situations, establish communication protocols with legal departments, law enforcement, and external partners, define roles and responsibilities across your incident response team, and implement training programs to ensure readiness.
Real-World Application
The methodologies in this repository align with industry best practices and complement other frameworks like ISO 27001 and CIS Controls. Organizations across all sectors use NIST’s incident handling guidance to manage breaches, ransomware attacks, insider threats, and other security events effectively.
By mastering these processes, you’ll be equipped to minimize incident impact, reduce recovery time and costs, preserve evidence for legal or forensic purposes, and strengthen your organization’s overall security posture through continuous improvement.
Conclusion
Cybersecurity incident handling is not optional—it’s a fundamental requirement for organizational resilience. This repository provides a structured pathway through NIST’s proven incident response framework, from initial preparation to post-incident learning.
Work through each module systematically, adapt the guidance to your organizational context, and practice your response procedures regularly. Effective incident handling minimizes disruption, reduces costs, and strengthens defenses against future threats.
The links above will take you directly to each resource—bookmark this page as your reference guide for building world-class incident response capabilities.
Stay prepared!