Email Forensics
Email remains one of the primary communication tools in modern business and personal interactions, making it a critical source of evidence in digital investigations. Whether you’re conducting corporate investigations, responding to security incidents, or building legal cases, understanding how to forensically analyze email data is essential for any digital forensics professional.
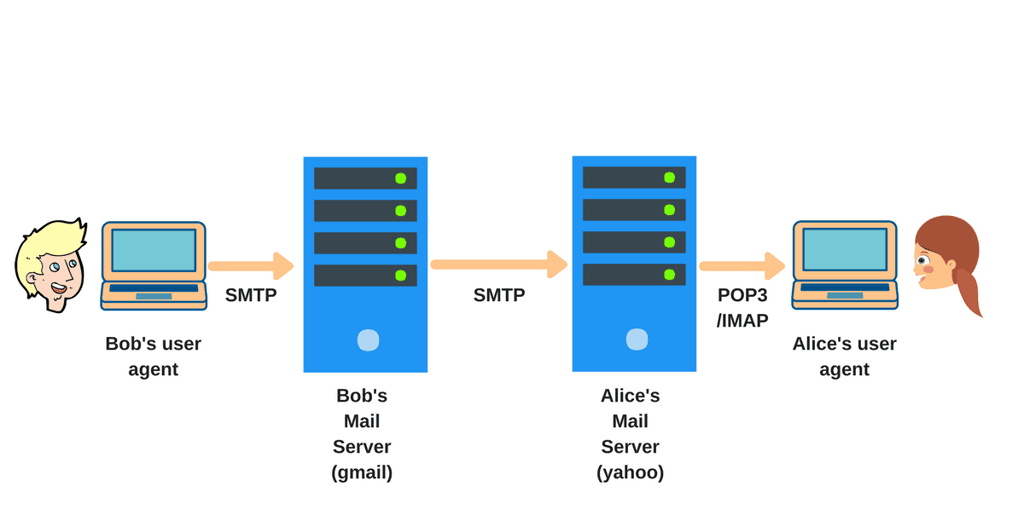
I’ve created a comprehensive repository that takes you through email forensics from foundational concepts to advanced investigation techniques. This guide serves as your navigation map—directing you to each resource and explaining what you’ll gain from it.
Repository: https://github.com/vsang181/LetsDefend/blob/main/Email%20Forensics/
What’s Inside
This repository contains seven detailed modules that cover the complete spectrum of email forensics, from understanding basic protocols to analyzing threat patterns and recovering deleted evidence. Each file provides focused, practical guidance you can apply immediately to real investigations.
How to Use This Repository
The modules follow a logical progression that builds your email forensics capabilities systematically. Start with Introduction to Email Forensics if you’re new to the field, then work through Understanding Email Protocols before diving into the analytical techniques. Experienced investigators can jump directly to specific analysis methods they want to enhance.
This repository teaches the three-stage forensic process: preservation, collection, and analysis—ensuring you maintain evidence integrity throughout your investigation.
Tools and Techniques
Throughout these modules, you’ll gain hands-on experience with forensic tools used by professionals worldwide. You’ll learn to parse email files in multiple formats, extract and verify metadata, track IP addresses and geolocate senders, authenticate digital signatures, reconstruct message routing paths, and recover deleted or hidden communications.
Advanced techniques include timeline analysis to visualize email patterns, link analysis to identify connections between suspects, and even skin tone analysis for investigating inappropriate imagery.
Real-World Applications
Email forensics skills are essential across multiple domains. Corporate investigators use these techniques to examine internal data breaches and policy violations. Law enforcement relies on email evidence for criminal prosecutions. Cybersecurity teams analyze phishing campaigns and malware distribution. Legal professionals need email forensics for litigation support and e-discovery.
By mastering the methodologies in this repository, you’ll be equipped to handle investigations in any of these contexts with confidence and precision.
Conclusion
Email forensics is a foundational skill in digital investigations, providing crucial evidence that can make or break a case. This repository offers a structured pathway from basic concepts to advanced investigative techniques.
Work through each module systematically, practice with real email samples in controlled environments, and apply these methods to actual investigations. The links above will take you directly to each resource—bookmark this page as your reference guide for email forensics excellence.
Happy investigating!